- 62% of organizational phishing simulations captures at least one user’s credentials.
- 27% of advanced Email attacks are being launched from compromised Email accounts.
- 95% of all attacks on enterprise networks are the result of successful spear phishing. It is not surprising that most of us have encountered numerous spam emails in our inbox and believe it or not, your online behavior contributes to the spam messages that you receive.
What are Spam/fake Emails?
- “Spam” has been an Internet buzzword since the dawn of email, but what is it, exactly?Spam/Fake emails are those messages which are randomly sent to multiple addresses by some people who are criminals or maybe lazy advertisers who wish to lead us to spoof sites.
- These sites attempt to steal our information such as personal, electronic, and financial.
How to recognize Spam/fake Emails?
There are many reasons to avoid interacting with spam mail, but then some of the truly troubling scenarios include the possibility that you’ll be putting yourself at risk for identity theft or allowing an attacker to load viruses and malware onto your computer. As a rule of thumb, if you want to avoid spam messages, it is important to remember that if something is too good to be true, then it probably is. This will help you weed out contests and offers that seem iffy.
Tips
Do not click on any button or link that you may see in spam messages. This may either lead you to malicious websites or download malware to your computer that can infect it. If any of the flags above are met, do not open the email. Just quickly move it to your trash bin. Deleted messages inside the Spam folder of your email will not go to the trash bin. They will be permanently removed from your account.
The above are some of the basic tips which need to be followed while opening any email. In this article, we are going to describe the tips and tricks to avoid such spam.
- 1. Make sure you know and trust the sender before opening an email
Since you can see who the sender is from your inbox list without having to open the message, you can ignore if a message is spam by simply looking at the sender’s email address. Some spam and phishing scams will pretend to be major companies.
2. Check the subject line for common spam topics
You already know most of these — sales, investment opportunities, and new treatments requests for money, information on packages you never ordered, etc. Usually, you are being offered something, often for nothing. If you didn’t order it, don’t assume you forgot. This is simply a scam tactic to make you click a bad link.
3. Avoid any “calls to action” or requests for personal information
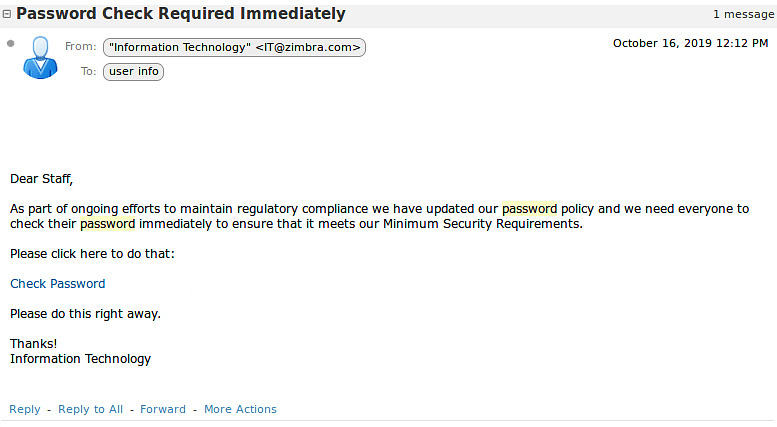
This is known as phishing when an attacker pretends to be a reputable site that has to “update user information,” or needs you to sign in “immediately.” In general, if the email asks for immediate action or personal information, it is phishing and should be ignored.
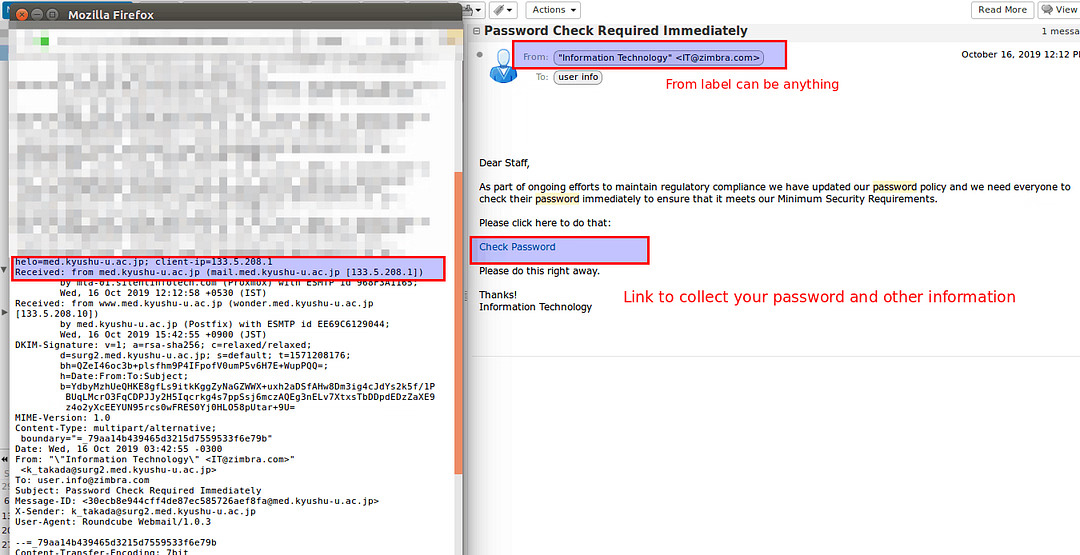
- For example – In the below image, it asks to “Check Password”.In order to find the original sender of an email, you can right-click on the email and click on the “Show Original” button, it will open up the original content of the email and you will find detailed information over there.
4. Never open or download attachments unless you know what they are
If you don’t know the sender, don’t trust a link and do not open any attachments. This is the quickest way to a virus. If you open the attachments, right-click on the first, then select “scan for viruses” or “scan” before opening.
5. Type in any links directly instead of clicking on the links
The most common way you’re information is compromised is by clicking a link in the spam email. However, if you’re unsure if the email is legitimate or spam, you still have options. For example, if you get a packaging email you weren’t expecting from Amazon, log on to Amazon and type in the order number to check it — don’t click on the “track package” link in the email.
6. Never use your business email address to register with third party websites, social media or any marketing portals
Do not use your personal or business email address when registering in any online contest or service such as applications, deal updates, etc. Many attackers watch these groups or emailing lists to harvest new email addresses.
7. Never Give out or post your Email publicly
You should remember that everyone can easily access the Internet. That means, attackers are also lurking on the Internet and are constantly seeking available email addresses which they will send spam emails to. Posting your Email address publicly allows others to send spam emails to you, or worse, hack your account if you are using a weak password.
8. Never use the same password everywhere
Let’s say you have an account at some online service – I’ll call it Service A. In addition, you have a Yahoo! account because you use Flickr, a Google account because you use Gmail and a number of other Google services, a Microsoft account because you have Windows. And you use that same wonderfully strong password everywhere. Service A has the best of intentions, but honestly, they don’t “get” security. Perhaps they store passwords in their database in plain text, allowing anyone with access to see them. They do that because it’s easy, it’s fast, and it allows them to solve the problem quickly. They make the assumption that the database containing your password will be impenetrable. This makes easy for the attackers to hack the sites and password.
9. Always browse through private or Incognito window
There are plenty of valid reasons to use private or Incognito browsing mode. You can use it to log into multiple emails, social networks, or bank accounts at the same time. This can prevent information or data from getting leaked from person to person.
- Google Chrome: Google Chrome calls it Incognito Mode, and you can tell you’re using it by looking for the “secret agent” icon in the top left corner of the window. Chrome also shows you a big, bold new tab page when you open an Incognito window. In Incognito Mode, Chrome won’t keep track of the pages you visit, the data you enter into forms, or any searches you submit. It won’t remember what files you download, but those files will stay on your computer after you close the Incognito window. You’ll have to manually delete them if you want them gone.

Mozilla Firefox
- Mozilla welcomes you to Firefox’s Private Browsing mode with a nice, clear explanation of what it does and doesn’t do.
Click on the top left corner of the window “ ” and click on the private window.
” and click on the private window.

10. On Public Computers (example – Cyber Cafe)
Extreme Caution. There are no guarantees about the programs installed and there may be programs to store passwords, installed by previous users.
If there is no other option for internet access, close all programs after use, log-off and clear the history in the browser (Tools / Options / Clear History) .In other practice, always browse through private or Incognito window when browsing through the Cyber Cafe.
Warning
Attackers are constantly refining and updating their spam. If something feels wrong, even if it is not on this list, play it safe and ignore the email.